Nobody can deny that they have never seen or downloaded pirated movies, actually without pirated movies life would get a tad bit boring. In recent times the pirated Version of the movies are available on the Internet on the same day of movie release. But before downloading pirated movies always check the release formats. Without the basic knowledge of different pirated movie formats you would be left with a bad copy of the film when other better prints were available for download. So i thought about writing about the popular pirated movie formats. Mostly the information is taken from wikipedia but i have also included my own opinions and experiences of the formats so if you want you can take a look at the wikipedia article. So here are the different formats arranged mostly in the sequence of their releases time.
Friday, May 20, 2011
Hacking Linkedin Passwords using Phishing
Linkedin is one of the most popular social networking site. So here is the phishing file for Linkedin to hack user passwords. DOWNLOAD
If you are not familiar with Phishing technique here is a detailed tutorial to carry out a phishing attack.
Note:- The phishing site looks exactly the same as the original. If you any suggestion about it please feel free to comment.
If you are not familiar with Phishing technique here is a detailed tutorial to carry out a phishing attack.
Note:- The phishing site looks exactly the same as the original. If you any suggestion about it please feel free to comment.
Monday, April 18, 2011
Cracking PDF User Passwords Or Editing Encrypted PDF ( Tutorial )
PDF has become one of the most popular and widely used file format. Today mostly all the ebooks are available in PDF format. But many times the PDF files are password protected by the creator or the owner. There are two types of password protection for the PDF files. A user password and owner password. The user password doesn't allow the user to open the file without entering the password and the owner password doesn't allow the user to print or edit the PDF file. There are many situation where you may find it necessary to crack this passwords like when you forget the user password to your personal PDF file or you may want to edit the file for what so ever reason or you may just want to crack the password because you can. There is no greater delight in computers then cracking of passwords. Here are methods to crack the both user and owner passwords using a software.
Labels:
CRACKING,
MULTIMEDIA HACKS
Thursday, April 7, 2011
SEARCHING PIRATED MOVIES (Beginners Guide)
Today one of the main use of the Internet is to see pirated movies. Many of the Internet users get a Internet connection especially for this. For a experienced netizen searching pirated movies is a child's play but the new and inexperienced users have a hard time finding the movies. Now searching for anything pirated is a art and it becomes more perfect after lots of experience. Also every user has his own techniques and tricks. Here i present you with some of the most popular ways of downloading or streaming pirated movies online.
STREAMING
If you have a fast Internet, streaming the pirated movies is best for you because you can see them right away, no need for completion of the download. Here are the most famous, reliable and fast video streaming websites.
STREAMING
If you have a fast Internet, streaming the pirated movies is best for you because you can see them right away, no need for completion of the download. Here are the most famous, reliable and fast video streaming websites.
Labels:
MULTIMEDIA HACKS,
TORRENTS
Tuesday, March 29, 2011
HACKING EMAIL IDs USING SMS & EMAIL BOMBERS
Hacker always come up with innovative ideas to hack email ids. Fake sms and email bomber softwares are one of them. Now let us have a look at how this sms and email bombers are used to hack email ids on a large scale. So what the hacker will do is, make a simple program with Graphical user interface using programing language like Visual Basic or Java (This basic programs are very easy to make if you have some knowledge of Visual Basic).
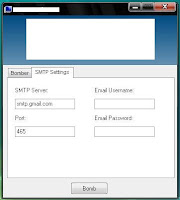 Here is a example of such a program. The GUI is kept very basic with minimum options. Now when the user fills the fields and presses "bomb" instead of doing its said work it will just deposit the username and the password in the hackers database and give the users some silly error like "Server busy" or "The target has blocked you" etc. So don't be surprised when you receive a email about Viagra or Porn sites because after collecting enough of this email ids the hacker will just sell them to above site owners.
Here is a example of such a program. The GUI is kept very basic with minimum options. Now when the user fills the fields and presses "bomb" instead of doing its said work it will just deposit the username and the password in the hackers database and give the users some silly error like "Server busy" or "The target has blocked you" etc. So don't be surprised when you receive a email about Viagra or Porn sites because after collecting enough of this email ids the hacker will just sell them to above site owners.
I am not saying that all this softwares are fake, there are some genuine software which really work. I have my self successfully tested SMS bombers.But they have their limitations. Do you really think that Gmail will allow anybody to bomb anybody? It will quickly understand your intentions and stop you.
So next time if a thought of bombing comes in your mind. Just pause for a minute and think, do you really want to do this? my personal opinion about bombing is that it is very childish and immature and if anybody gets satisfaction or happiness by doing such dumb things then he should get some psychological help.
 Here is a example of such a program. The GUI is kept very basic with minimum options. Now when the user fills the fields and presses "bomb" instead of doing its said work it will just deposit the username and the password in the hackers database and give the users some silly error like "Server busy" or "The target has blocked you" etc. So don't be surprised when you receive a email about Viagra or Porn sites because after collecting enough of this email ids the hacker will just sell them to above site owners.
Here is a example of such a program. The GUI is kept very basic with minimum options. Now when the user fills the fields and presses "bomb" instead of doing its said work it will just deposit the username and the password in the hackers database and give the users some silly error like "Server busy" or "The target has blocked you" etc. So don't be surprised when you receive a email about Viagra or Porn sites because after collecting enough of this email ids the hacker will just sell them to above site owners. I am not saying that all this softwares are fake, there are some genuine software which really work. I have my self successfully tested SMS bombers.But they have their limitations. Do you really think that Gmail will allow anybody to bomb anybody? It will quickly understand your intentions and stop you.
So next time if a thought of bombing comes in your mind. Just pause for a minute and think, do you really want to do this? my personal opinion about bombing is that it is very childish and immature and if anybody gets satisfaction or happiness by doing such dumb things then he should get some psychological help.
Labels:
SECURITY TIPS,
SOFTWARE DEFACED
Saturday, March 19, 2011
FIREFOX HACKING ADDON ( HackBar )
This toolbar will help you in testing sql injections, XSS holes and site security. It is NOT a tool for executing standard exploits and it will NOT teach you how to hack a site. Its main purpose is to help a developer do security audits on his code. If you know what your doing, this toolbar will help you do it faster. If you want to learn to find security holes, you can also use this toolbar, but you will probably also need a book, a lot of Google and a brain :).Using this addon you wont have to open your notepad every time you need to compose scripts.
FEATURES
- Even the most complicated urls will be readable
- The focus will stay on the textarea, so after executing the url (Ctrl+Enter) you can just go on typing / testing
- The url in textarea is not affected by redirects.
- On the fly uu/url decoding.
- All functions work on the currently selected text.
- MD5/SHA1/SHA256 hashing
- MySQL/MS SQL Server/Oracle shortcuts
- XSS useful functions
- And lots more !!!
DOWNLOAD
Labels:
FIREFOX ADDONS
Tuesday, March 15, 2011
HACK YOUR CPU FAN (using speedfan)
One of my PC at home has a Celeron processor. As my other two PCs where having some hardware problem i had to resolve to this Celeron processor. It used to frequently get overheated while playing games and due to the overheating the computer used to turn off automatically, so i started playing around with my CPU fan settings. Here are some tweaks i did,
1) First i went to the bios settings and disabled the "smart fan" option.(Smart fan is used to reduce the fan noise, what it actually does is increases the fan's speed only when needed. But it was bad for the Celeron as the max temp limit of Celeron processor is less compared to other Intel Processors, so while the "Smart Fan" increased fan's speed it would be already late and the PC would just turn off. Without "smart fan" the Fan's speed was high enough to keep the Processor from heating up quickly)
2) I still had some problem so i installed a software called "SpeedFan" (SpeedFan is a program that monitors voltages, fan speeds and temperatures in computers with hardware monitor chips. SpeedFan can even access S.M.A.R.T. info and show hard disk temperatures. SpeedFan supports SCSI disks too. SpeedFan can even change the FSB on some hardware (but this should be considered a bonus feature). SpeedFan can access digital temperature sensors and can change fan speeds accordingly, thus reducing noise. SpeedFan can find almost any hardware monitor chip connected to the 2-wire SMBus (System Management Bus (trademark belonging to SMIF, Inc.), a subset of the I2C protocol) and works fine with Windows 9x, ME, NT, 2000, 2003, XP, Vista and Windows 7. It works with Windows 64 bit too. )
DOWNLOAD SPEEDFAN
I have no idea why only this piece of software worked, from the many fan control softwares, but it worked for me and now i can play all the games without my PC automatically turning off.
NOTE:- If you too are facing the same type of problem you are welcome to share your problem with us.
1) First i went to the bios settings and disabled the "smart fan" option.(Smart fan is used to reduce the fan noise, what it actually does is increases the fan's speed only when needed. But it was bad for the Celeron as the max temp limit of Celeron processor is less compared to other Intel Processors, so while the "Smart Fan" increased fan's speed it would be already late and the PC would just turn off. Without "smart fan" the Fan's speed was high enough to keep the Processor from heating up quickly)
2) I still had some problem so i installed a software called "SpeedFan" (SpeedFan is a program that monitors voltages, fan speeds and temperatures in computers with hardware monitor chips. SpeedFan can even access S.M.A.R.T. info and show hard disk temperatures. SpeedFan supports SCSI disks too. SpeedFan can even change the FSB on some hardware (but this should be considered a bonus feature). SpeedFan can access digital temperature sensors and can change fan speeds accordingly, thus reducing noise. SpeedFan can find almost any hardware monitor chip connected to the 2-wire SMBus (System Management Bus (trademark belonging to SMIF, Inc.), a subset of the I2C protocol) and works fine with Windows 9x, ME, NT, 2000, 2003, XP, Vista and Windows 7. It works with Windows 64 bit too. )
DOWNLOAD SPEEDFAN
I have no idea why only this piece of software worked, from the many fan control softwares, but it worked for me and now i can play all the games without my PC automatically turning off.
NOTE:- If you too are facing the same type of problem you are welcome to share your problem with us.
Labels:
HARDWARE TWEAKS
Thursday, March 10, 2011
HACKING VKONTAKTE USING PHISHING
I had many requests for phishing page of Vkontakte (Russian social networking site), so here is the Phishing file for it DOWNLOAD
For a detailed tutorial on Phishing check out my Phishing tutorial for beginners. Click Here to go to Phishing Tutorial.
For a detailed tutorial on Phishing check out my Phishing tutorial for beginners. Click Here to go to Phishing Tutorial.
Thursday, February 10, 2011
ADDING BACKDOOR IN HACKED FACEBOOK ACCOUNTS
Here is a way how some hackers retain the hacked facebook accounts even after the target changes the password or the hacker himself returns it to the target.
Many of the facebook users are unaware that there is a alternative way to log in the facebook account by linking a alternate email account to it. Not the default email id which you use regularly to log in by typing the email id and password but a different email id. So when you are logged in this alternate email id and open the facebook website it directly logs in your facebook account without even asking the password. If you did not get the concept here is a example. Imagine that your regular email id is "regular@gmail.com" and you add a alternate email id "alternate@gmail.com" in account setting. Now when you are logged in "alternate@gmail.com"
and open facebook website it redirects you and directly opens your facebook account. So here the is procedure how you can add this alternate email id as a backdoor.
Many of the facebook users are unaware that there is a alternative way to log in the facebook account by linking a alternate email account to it. Not the default email id which you use regularly to log in by typing the email id and password but a different email id. So when you are logged in this alternate email id and open the facebook website it directly logs in your facebook account without even asking the password. If you did not get the concept here is a example. Imagine that your regular email id is "regular@gmail.com" and you add a alternate email id "alternate@gmail.com" in account setting. Now when you are logged in "alternate@gmail.com"
and open facebook website it redirects you and directly opens your facebook account. So here the is procedure how you can add this alternate email id as a backdoor.
Tuesday, February 1, 2011
FIRESHEEP TUTORIAL (Http Session Hijacking)
Firesheep a Firefox addon has recently become very popular for easily carrying out a HTTP session hijacking attack. Http session hijacking attack can't be considered as a very sophisticated attack but needs some technical knowlegde to be performed . But Firesheep makes the attack a child's play. Firesheep was developed by Eric butler for Firefox, it was released at Toorcon 12 to demonstrate how serious cookie stealing can be.
Now lets understand how Firesheep actually works. When you provide your username and password in login forms of different website and submit it, the browser first encrypts the password and then sends it over the network. The corresponding website compares the information against its internal database and if they match, it sends a cookie(a small text file) to your browser. The browser saves this cookie and uses it to authenticate the user on the website every time the user opens a different page of the website. When the user logs out of his account the browser just deletes the cookie. Now the problem is that this cookies are not encrypted before sending over the network, due to this a hacker can capture this cookies and using them authenticate himself as the user from whom the cookie was stolen.
Now lets see how to use Firesheep.
Now lets understand how Firesheep actually works. When you provide your username and password in login forms of different website and submit it, the browser first encrypts the password and then sends it over the network. The corresponding website compares the information against its internal database and if they match, it sends a cookie(a small text file) to your browser. The browser saves this cookie and uses it to authenticate the user on the website every time the user opens a different page of the website. When the user logs out of his account the browser just deletes the cookie. Now the problem is that this cookies are not encrypted before sending over the network, due to this a hacker can capture this cookies and using them authenticate himself as the user from whom the cookie was stolen.
Now lets see how to use Firesheep.
Monday, January 31, 2011
REVEALING PASSWORD HIDDEN BEHIND ASTERISKS
When you type a password in the password form while logging into any of your account the letters of the password are hidden behind asterisk, so that nobody can have a sneak peak at your password. But many times you may want to know whats behind the asterisks. Here are some methods to reveal the passwords behind asterisks.
1) Using Javascript
Using a simple javascript you can reveal all passwords behind the asterisks, here is the procedure.
1)Open the webpage containing the login form with the password behind the asterisks.
Monday, January 17, 2011
SECURITY REDEFINED (Make your drive unhackable)
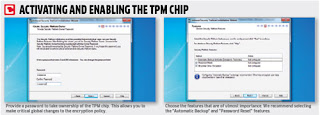
Make your drive virtually unhackable by enabling TPM on your machine.
We all know how easy it is for snoopers to get their hands on private and confidential data. That’s the main reason we need to constantly refine our security policies to keep confidential data safe. While there are many software applications that will do the job they could be easy to crack; at least for a seasoned hacker. That’s not the only reason to be worried. Imagine losing your laptop or even your portable drive which contains important data.
What we are referring to is hardware based encryption rather than the more common software based methods. To begin with you will need a PC with a motherboard that has an embedded TPM (Trusted Platform Module) chip. So before we even get into the intricacies of setting up the encryption system, let’s go a little further and understand the basic functionality of a TPM based motherboard.
Tuesday, January 11, 2011
HACK FACEBOOK PASSWORD USING EASY METHODS
 Facebook is the latest teenage craze all around the world. I have seen many people wasting hours for finding different methods and ways for hacking their friend's or enemy's facebook account. Most of the sites claiming to teach easy facebook hacking methods are spam and try to sell you useless hacking ebooks or other senseless softwares.Some even claim to hack the facebook passwords for free for you. Wake up people and think logically. First let me make something clear to you, there is no such software or tool which will hack the Facebook account password for you, while you sit back and enjoy your cappuccino and don't even think of hacking into the facebook databases to get the passwords. But hacking facebook accounts is not completely impossible, i would say it can be done rather very easily if you decide to give your time and have some patience. There may be hundreds of ways to hack facebook account password, but here i am providing you some, which i am familiar with. This is a long post and i have tried to provide all the methods in great detail so bear with me.Now let us begin.
Facebook is the latest teenage craze all around the world. I have seen many people wasting hours for finding different methods and ways for hacking their friend's or enemy's facebook account. Most of the sites claiming to teach easy facebook hacking methods are spam and try to sell you useless hacking ebooks or other senseless softwares.Some even claim to hack the facebook passwords for free for you. Wake up people and think logically. First let me make something clear to you, there is no such software or tool which will hack the Facebook account password for you, while you sit back and enjoy your cappuccino and don't even think of hacking into the facebook databases to get the passwords. But hacking facebook accounts is not completely impossible, i would say it can be done rather very easily if you decide to give your time and have some patience. There may be hundreds of ways to hack facebook account password, but here i am providing you some, which i am familiar with. This is a long post and i have tried to provide all the methods in great detail so bear with me.Now let us begin.1) KEYLOGGING
Type:- software and hardware
Tools needed:- Keylogger software or keylogger device
Special skills needed:- no special skills needed but some commonsense , some prior knowledge of the target and convincing power.
Main enemy:- Antivirus software and Firewalls.





